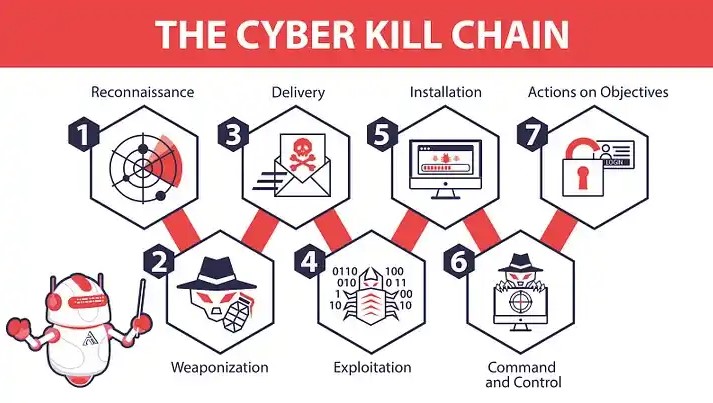
There are script kiddies who succeed blindly and there are black hats who have larger fish to fry. This second chapter helps to draw a picture somewhere in the middle between the basement movie scene and the super-secret-squirrel black hat. Referencing the Lockheed Martin Cyber Kill Chain, there are 7 distinct steps a white hat, gray hat, or black hat can follow to execute a cyber attack. There are other methodologies and frameworks out there on the internet but we are starting here with How Cybersecurity Really Works to build a foundation. Take a quick glance at this article on Medium.com about the CKC, Diamond Model, & MITRE ATT&CK (or add it to your add-rabbithole-to-do list).
The Lockheed Martin Cyber Kill Chain 7 steps are…
- Reconnasissance
- Weaponization
- Delivery
- Exploitation
- Installation
- C2
- Attack
Reconnasiance. I assume we all know what recon is. Who ate the last bowl of corn pops and left the empty box in the cabinet? You would do your due diligence to gather intel on who/what/when/where/why. Collecting data is important in preparing for an attack but it is also important in knowing your own surroundings and network to prevent an attack. Familiarization with the attack methodology will increase awareness of your own home network and overall security knowledge. Collecting data does not have to look like a science experiment or a pie chart. It can be as simple as scrolling through someone’s many socials: Facebook, X, TikTok, Snapchat, Linkedin, Youtube, Reddit, other forums, Github, tagged photos, public posts, employees, employers, and ex-boyfriends. It can also be a tad more fancy such as scanning a network with Wireshark or looking for open ports with Nmap.
Weaponization. Brainstorm, plan, identify, and prioritize. Creating a plan and identifying a target results in the weaponization of the attack.
Delivery is not the actual delivery of the attack but rather identifying the method of delivery. How will malware be implanted? Will a phishing email be sent to an entire organization email distribution? Will the email have a link to a hijacked URL or a cloned banking webpage? Maybe finding a customer contact form that does not have data validation so you can deliver via cross-site scripting?
Exploitation. The attacker has a target and a method of payload delivery. The delivery method might be seem to be the exploit but it is not. Finding a way into a system, or creating the opportunity to access a system, is providing a backdoor into the system. Now, what network or system resources will be exploited? A methodical attack is likely seeking a long term effect, a large financial gain, or a to make a statement. The above mentioned delivery methods allow an opportunity to exploit. Once a end-user or system falls victim to the delivery method, then the target can be exploited. Maybe a small business owner pays a service to create a website and the customer contact form falls victim to cross-site scripting. The attack could possibly gain internal access to the site’s server and from there continue to working towards the owner’s database. Check out OWASP’s XXS article.
Installation. They have found the backdoor. They are inside now but not all attacks are instant. Perhaps the delivered payload is waiting for a particular time or condition to be met such as creating XXX amount of bots with the intention of creating a several botnets with the intention of a larger attack after initial infection. Maybe an end-user fell victim to social engineering by clicking the verification link that the “Verizon” representative text to his cell phone. That link could have installed a malicious file on the users device. The possibilities are endless.
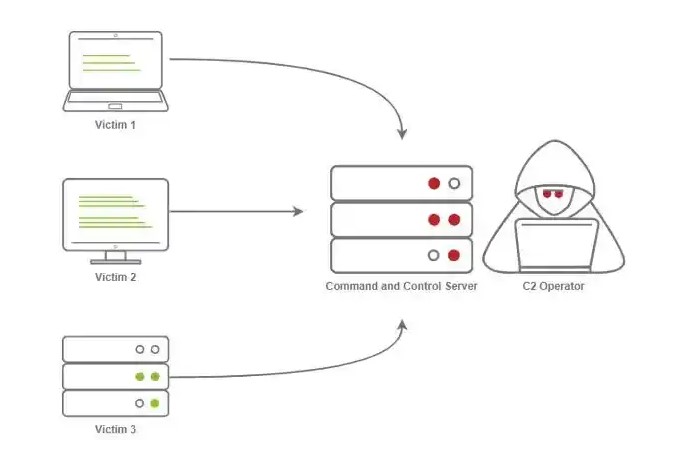
Command and Control, aka C2. Script kiddies and black hats certainly have one thing in common– they do not want to get caught. Utilizing C2 facilitates remote monitoring and remote execution. An attacker can pivot through as many methods of weaponization, delivery, exploitation, installation, and attacks, as their heart (or plan) desires. They can do so, from the comfort of their own chair.
Attack. This last steps is also known as “actions on objectives” by Lockheed Martin. There is where everything comes into place for execution.
Exercise 2: Analyzing your Network
Having insight on various attack methodologies should enhance end-user’s awareness of safe practices when using the internet. Now, we’re going to learn more about analyzing our own networks and try to identify vulnerabilities using a few basic tools. Just like the first step of the CKC, we’re going to do some recon of our own. NOTE: Do not share or publish data such as your personal devices MAC’s or public IP’s. You can, but you shouldn’t.
To name a few, here are identifiers we should be weary of accessing and sharing on the internet: personal email addresses, documents, file types, downloads, desktop applications, mobile applications, IoT devices, geotagging, Google searches, metadata, pixels, geotagging, tagged posts, tagged photos, public work email addresses, site alas’, broadcasted SSID’s, hardware & software with default credentials, MAC’s and IP’s, and whatever else you can find physically or logically (on the computer screen). Sam Grub mentions what we put on the internet can be open, public, and forever, quite a few times in chapter 2. We should heed this with everything we create, store, and transmit. Unless your lawyer is dissecting ready every ToS you agree to, it is unlikely you could explain what these third party services are accessing on our mobile devices, tablets, files, data, etc.
Oh. You don’t do social media. Got it. Did you ever have Myspace or AOL chat? Does your cousin who takes 70 photos at every family event post family photos online? Home security services backed up to the cloud, internet connected washing machines, Bluetooth connected smokers, fitness trackers that have location services enabled 24/7. Although you might not necessarily make yourself public, the internet is forever and has endless resources to archive all data.
Check out https:\\archive.org\.
Command Line (Terminal) & Shodan
Unless you have applied the security best practices, it is likely your SOHO it at risk of an attack. I will go over the best practices after reviewing a few tools commonly used.
If you are green like me, you cannot accomplish much with Shodan if you don’t know what you are doing or what your are looking for. We will use command line to help give us data to search using Shodan. Using command line will help but first let us identify your public IP with a quick Google (or DuckDuckGo or Brave) then recourse to command line. Try searching your browser for Myip.ms. Myip.ms will query results similar to the following.
| IPv4 Address: xxx.xxx.xxx.xxx |
| ISP: BestInternetServiceProviderEver |
| Proxy detected? Yes/No |
| Your location: Bikini Bottom, OC. |
| Your browser: AOL |
| Your OS: Microsoft Windows 1.01 |
Navigate to command line. Windows operating systems use Command Line or Command Prompt while Mac uses terminal. CLI is short for command line interface. Using CLI and terminal are similar in function but differ in syntax. Typing -help or -man in the prompt or an internet search will get you a manual. Here is a short list of commands to get started with.
- Command Line
- ipconfig
- nslookup
- ping
- tracert
- Terminal
- ifconfig
- ping
- traceroute
Now, identify your private IP using ipconfig (in Windows) and ifconfig (in Mac). Having identified the private IP, we can move on and notate other important information about our network. Ipconfig has several options; however, ipconfig is suitable to get started. Remember, each additional argument will report more data. The purpose of this exercise is to familiarization; you can always come back to further explore. Now, stop, go to CLI, and run ipconfig. You will see something similar to the following.
| ipconfig | ||
| wireless LAN adapter wifi | ||
| connection specific DNS suffix | ||
| description | Inetl (R) Wifi AA### | |
| physical address (MAC) | 00-A7-7A-77-A7-77 | |
| DHCP enabled | yes | |
| link-local IPv6 address | aa00::a000:0000:0000:0x0000 | |
| IPv4 address | xxx.xxx.xxx.xxx ex: 192.168.86.xxx | |
| subnet mask | 255.255.255.0 | |
| lease obtained | 07/13/2089 15:52:06 | |
| lease expired | 07/15/2089 15:52:06 | |
| default gateway | xxx.xxx.xxx.xxx ex: 192.168.86.0 |
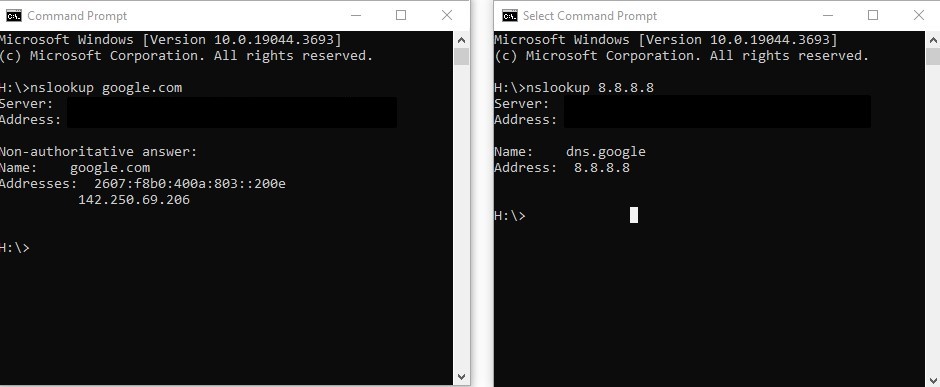
Let’s nslookup Google or whatever site you want to check. Go to CLI and type “nslookup google.com” . It should display the domain name and host IP. Or begin the search with the opposite, begin with the IP. Go to CLI and type nslookup 8.8.8.8. Try this with a few other sites.
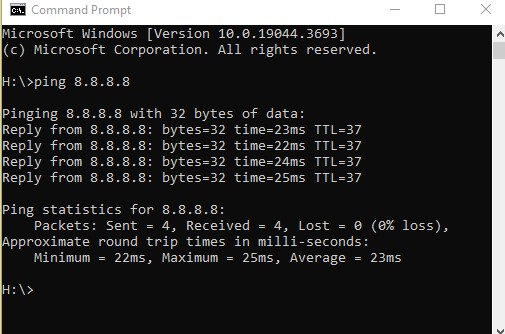
Ping, ping, ping. There are many flavors of ping. For now, ping to identify connectivity or lack of connectivity. First ping a target, then ping the gateway, and then maybe the server. The manual better explains ping as, “Verifies IP-level connectivity to another TCP/IP computer by sending Internet Control Message Protocol (ICMP) echo Request messages. The receipt of the corresponding echo Reply messages is displayed, along with round-trip times. ping is the primary TCP/IP command used to troubleshoot connectivity, reachability, and name resolution.” This will help answer important questions. You can ping IP addresses and FQDN’s. For Mac users, ping is still ping.
Is the host/device receiving the echo request?
Is the host/device responding to the echo request?
How long is it taking to receive? How long will it take before it stops trying?
Were the packets sent, received, or lost?
All of those questions are important in identifying connectivity between devices, networks, and servers. The more information available to the internet and public, the more vulnerabilities there are. Familiarization with your own network will help better understand what to keep an eye out for.
Tracert tells you how many hops, how long the hops are (from one router to the next), and where the hops are. “This command determines the path by sending the first echo Request message with a TTL of 1 and incrementing the TTL by 1 on each subsequent transmission until the target responds or the maximum number of hops is reached. The maximum number of hops is 30 by default…“, but with added parameters, you can do things like specify how many hops to take or how many milliseconds to allow for an echo response. Essentially the father apart host are, there will be more hops and more time apart. Traceroute is the command for terminal.
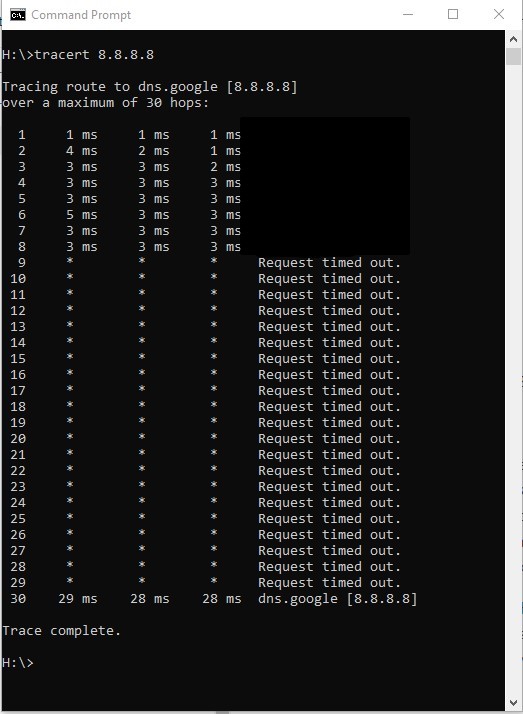
That is about it for chapter 2’s tools for analyzing your own network. I decided to take one more step which was applying security best practices (if not done already).
SOHO Security Best Practices
Here is a side-by-side from a few sources. Most of the recommendations are similar however browsing through each of the links separately will provide a bigger and better picture. It is important to become familiar with methodologies and best practices but it is more important to understand what is you’re looking at before acting on those best practices. I implore you to investigate your own network and become familiar before making changes.
| Best Practices For Securing Your Home Network | How To Secure Your Home Wi-Fi Network | Lock Down Your Network: 10 Expert-Recommended Tips for a Secure Home Wi-Fi | Secure Your Wireless Router: 8 Things You Can Do Right Now | Securing Your Home Network |
|---|---|---|---|---|
| Keep it up-to-date | Keep your router up to date | Keep your router and devices up to date | Update the Firmware | Run a Clean Machine |
| Limit use of the administrator account | Change routers deault settings | Change the default router login credentials | Change Default Login Credentials | CHANGE THE PRESET PASSWORD ON YOUR ROUTER |
| Secure routing devices and keep them up-to-date | Set up a guest network | Create a guest network | Lock Down Wi-Fi Access | CREATE A GUEST NETWORK |
| Employ firewall capabilities | Turn on your router firewall | Turn on firewall | Log Out of the Router’s Web Interface When You’re Done Configuring It | USE A FIREWALL |
| Implement WPA3 or WPA2 | Encrypt your network | Turn on Wi-Fi encryption | Disbale Remote Access | REVIEW SECURITY OPTIONS |
| Implement wireless network segmentation | Use WPA2 or WPA3 | Upgrade to a WPA3 router | Disable UPnP | CHANGE THE NAME OF YOUR ROUTER |
| Leverage security software | Log out as administrator | Create a strong Wi-Fi password and change it often | Change the Router’s Local IP Address | |
| Protect passwords | Disable remote router access | Install Third-Party Firmwares | ||
| Upgrade to a modern operating system | Turn off “remote management” | Place your router in a central location | ||
| Safeguard against eavesdropping | Turn off UPnP | Use a VPN | ||
| Exercise secure user habits | Turn off WPS | Verify connected devices | ||
| Limit administration to the internal network only | ||||
| Schedule frequent device reboots | ||||
| Ensure confidentiality during telework |
The End
Go forth and do great things. Like identifying your SOHO public IP, private IP, ISP’s gateway, and other data from ipconfig, ping, nslookup, and tracert. Search those in Shodan. Then try to identify vulnerabilities that can be addressed such as changing the default login to your router or disabling remote management.