“I HAZ COFFEE WHEREVERS. Please, I can haz credit card number? K. Thx. BAI.”
My goal is to stay organized. So, here are the main learning objectives.
- familiarization of phishing attacks
- identify various types of phishing attacks
- identify practical tools to assist in analyzing phishing attacks
User Awareness
End-users do not have to go far to find phishing attempts. In fact, most users fall victim through seemingly legitimate techniques. Pondering on my younger years of using AOL and Yahoo, I most certainly clicked those hidden redirect links and unsubscribe here links. How has my identity not been compromised? What are some personal examples of phishing attempts you have seen? Even if you cannot recall immediately, hopefully after this exercise you are able recognize the malicious intent of phishers.
- Do not trust unknown or unexpected senders (or domains)
- Do not trust unknown or unexpected attachments (or file formats)
- Do not trust unknown or unexpected links (or webpages)
Don’t trust unknown OR unexpected senders, attachments, or links
Identifying untrustworthy senders might be visibly obvious but that is not always the case. The majority of the end-user training found online highlight not trusting the unknown; it is less common to find training highlighting the unexpected. Unexpected should be emphasized equally because it too could avoid heartache. User Salena receives an email from an unknown sender and a weird attachment. Curious and having the habit of tending to her emails promptly, she opens it. Although she is using her official work email, the sender doesn’t have an official certificate demonstrating their trustworthiness. She isn’t sure about the attachment though. Without going down a rabbit-hole of possible malicious outcomes, Salena failed to recognize most of the basic tips & tricks. User Ricky is among 30 employees (or students) who received the same phishing email. In addition to this email being from an unknown sender and providing several links, he recognized the email and links were oddly unexpected. Since Ricky has had a few phishing trainings over the years, he was able to identify several red flags and ultimately deleted the email. Perhaps he reported it to the security or IT team so they could prevent other unprepared end-users from accessing similar emails.
Visit official websites rather than using the provided links
Even if a link seems legit, it would be wise to not trust. There are two very simple options end-users can use to avoid falling victim. One, copy and paste is a very easy and overlooked tool. Pasting the link into a notepad will allow the full URL to be read. A URL can be further analyzed but to keep to the basics for now, if the full URL looks funky, stay away. The second simple option is to visit official websites rather then the provided one.
Be familiar with phishing tactics to avoid falling victim
Phishing tactics vary. They can be super simple and pray upon the lack of user-knowledge. They can be intermediate through layering several tactics in hopes of increasing a successful phish (intimidation, friendly naming conventions, targeted information, hijacked domain). They can also be sophisticated such as using an Evil Twin (mimicking a legit website) paired with several redirects. Keep reading below for a broader familiarization.
Tactics
Phishing is a favorable method for targeting end-users due to its high success rate and cheap cost. All risk cannot be eliminated however with regular user training and a few online tools, the number of successful phishing attempts can be reduced. Some emails may be obviously suspicious but others can be highly deceiving. There are a variety of tactics that professional arses use to trick end-users of all types. First, let’s cover a few basic social engineering ploys that are likely to be in phising emails.
- Back to the basics. If the grammar and spelling are both terrible, chances are, you’re being phished. “I HAZ COFFEE WHEREVERS. Please, I can haz credit card number? K. Thx. BAI.”, https://gooogle.com, https://A0Lmail.com.
- Urgency, Intimidation, & Authority. If the sender sounds like an informercial offering a once-in-a-lifetime-deal or explicitly instructing a password change through a red link, assume it is untrustworthy. “We have missed you in attempting to deliver your Amazaon package. Please click Here to verify our delivery attempt”.
- Prizes and Monetary Gain. This could be considered an extension of urgency because anyone in their right mind could not pass up such a great opportunity to claim their free life-time supply of Milk Bones. From pocketing gift cards to being hand-selected for a grand prize, a financial gain can be enticing to many. Whether an end-user feels special for being selected, has FOMO, or not very tech saavy, a phishing attempt can have a negative connotation or a positive one. A positive example would be receiving a life-time supply of Milk Bones while a negative example could be a supposed credit union emailing about your over due payment. “But hurry! If you don’t act now, you could miss the last chance for this world-class cruise valued at over threethousand dollars!”
Types of Phishing
- Spear Phishing- Being individually targeted or the sender is impersonating a real person
- Whaling- Targeting executive level members
- Vishing- voice or audio calls to phish information such as audio recordings, account info, etc.
- Pharming- A redirection through webtraffic in hopes of gathering user credentials
- Smishing- SMS or text phishing
- Quishing- QR code
- Other related and notable terms
- Evil Twin- Malicious resources disguised as reputable resources such as the Amazon logo or other registered trademarks being used on a faked website
- Watering Hole- targeting high trafficked areas
- Typosquatting- Extremely reputable organizations are known to buy domains that are similar to theirs but mispelled, locating a mispelled domain not already owned can be bad
- Complex URL’s- URL’s too difficult to read or a path that does not make sense, like seeing a unrelated domain or a link within a link
- Redirects- Some redirects immediately trick users but some will redirect multiple times hoping the user believes the session timed out. The final redirected “login page” could be an Evil Twin.
Tips & Tricks
Learning how to analyze different parts of an email is not out of a beginners reach with the use of a few free and super simple online tools. Let’s begin at the top and work towards the bottom of an email.
Beginner Analysis of Email Components
- “From”
- “To”
- Email Body
- Email Links & Attachments
- Email footer
From. At first glance, the “from” might appear trustworthy. A lot can be told viewing the entire contact information. Perhaps you don’t recognize the senders domain, the domain is misspelled, or the name of the real person you know is spelled incorrectly. There are indications of a phishing attempt.
To. Was the email sent to a specific department? An entire organziation? Or only sent directly to you? The “to” should match the bodies targeted audience.
Body. Keep an eye out for inaccurate information or odd information. Be weary of account numbers, reference numbers, and other detailed information. It is unlikely organizations should be emailing this. The basic tips and tricks apply.
Links & Attachments. Users can hover over links, right click for more options, or copy and paste them into a notepad for further analysis. The basic tips and tricks apply.
Organizations footer/bottom links. A quality phishing email can and will mimic an organizations email signature panel, logos, and footer to seem legitimate. The basic tips and tricks still apply!
Header Analysis w/ Mx Toolbox
First off, what is a header analysis? A header analysis can be completed by using a tool to sift through raw data to help understand better what is being displayed on the screen. There is more to face value. Here we are utilizing a free and web-based tool called Mx Toolbox. The tabs shown are SuperTool, Mx Lookup, Blacklist, DMARC, Diagnostics, Email Health, DNS Lookup, Analyze Headers.
Second, select Analyze Header
Third, navigate to the email to be analyzed
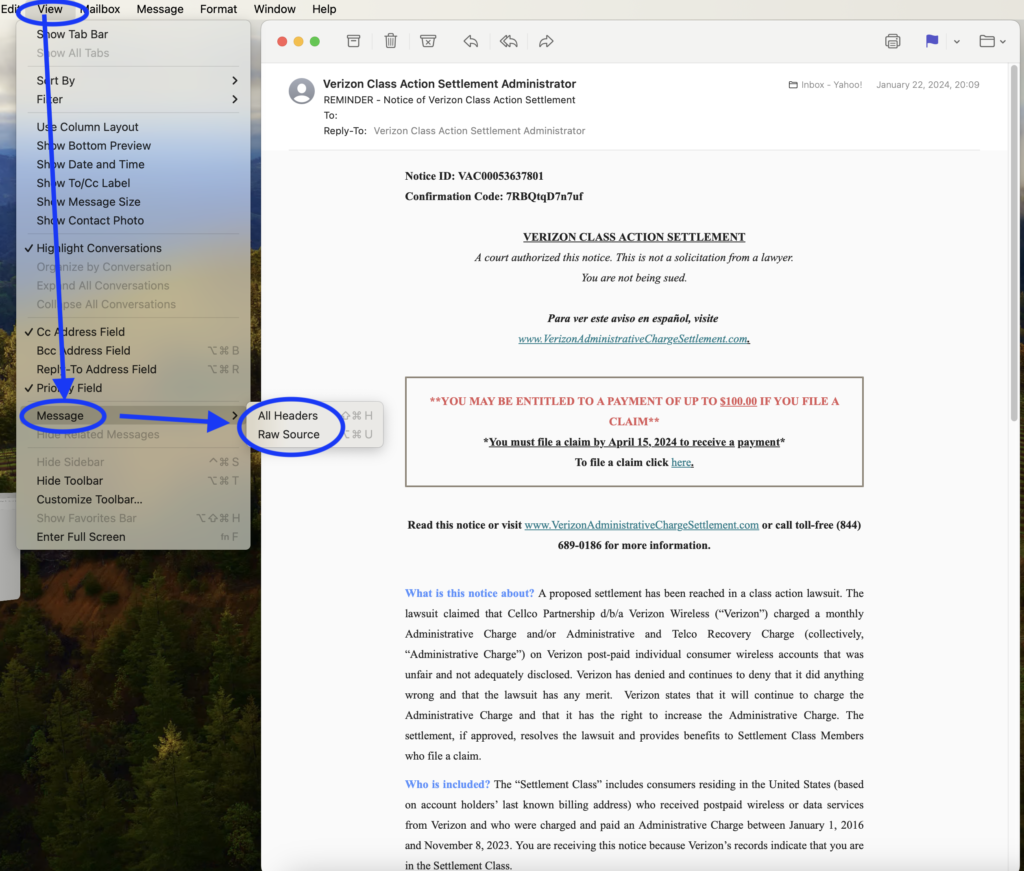
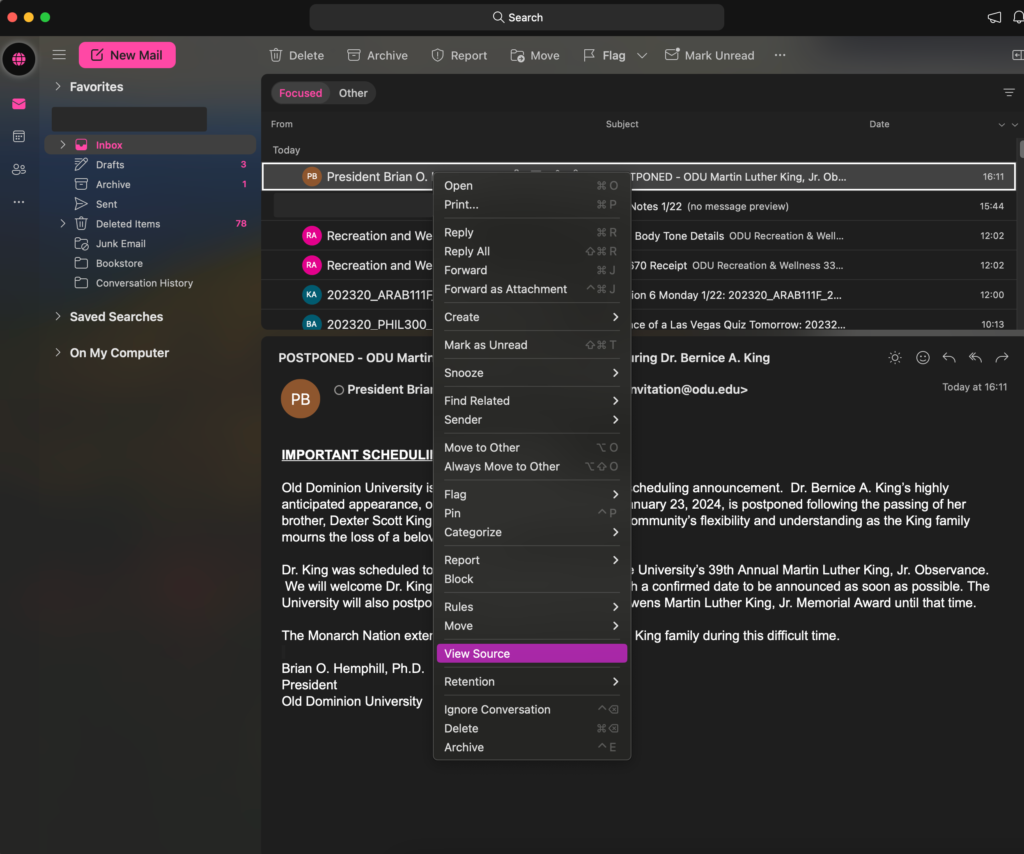
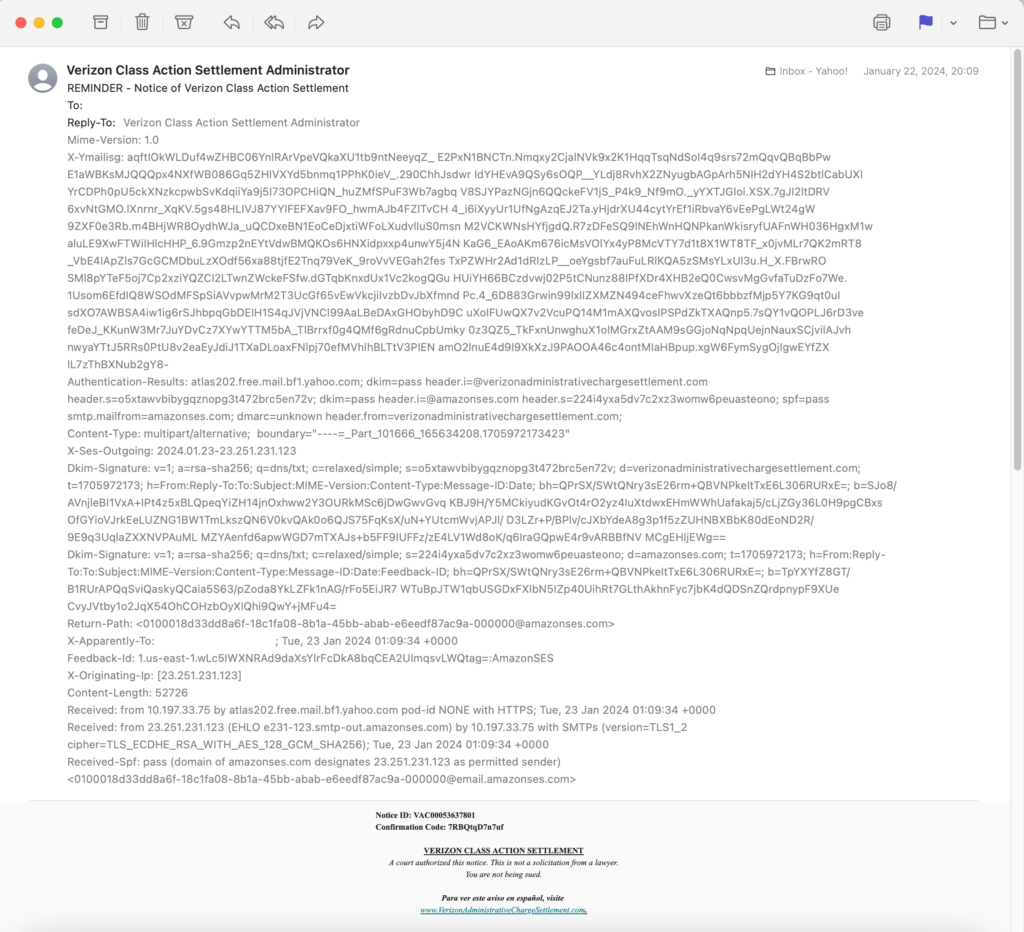
Fourth, locate the email header. Here are two examples. One for Outlook and one for Apple. Once you locate the header of your target email, copy the full header.
- For Apple, open a particular email in separate window. I had to access the full header on the desktop. I could not access the header with the native ‘ mobile or tablet email application. You can first open (1) all headers and then (2) raw source so you can compare the two for your own future knowledge. See example below.
- For Outlook, I also used the desktop application. Hover over the email to be analyzed, right click, and scroll down to “View Source”. See example below.
Fifth, visit Mx Toolbox, select the Analyze Headers tab, and paste header into the giant empty box.
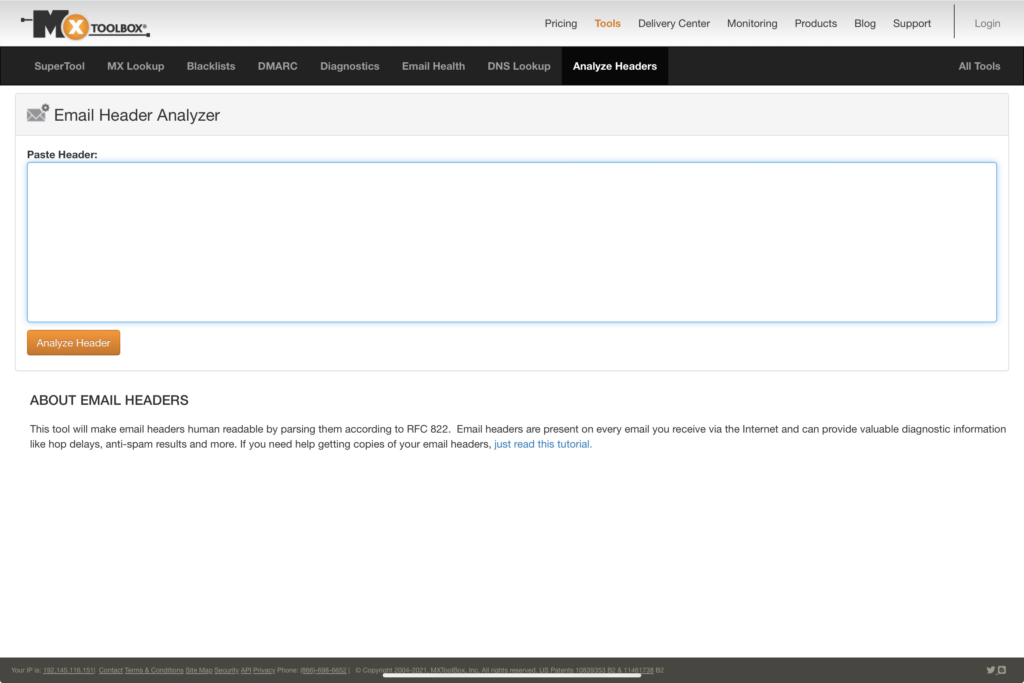
Six, select the orange Analyze Header button.
Viewing and Understanding Results
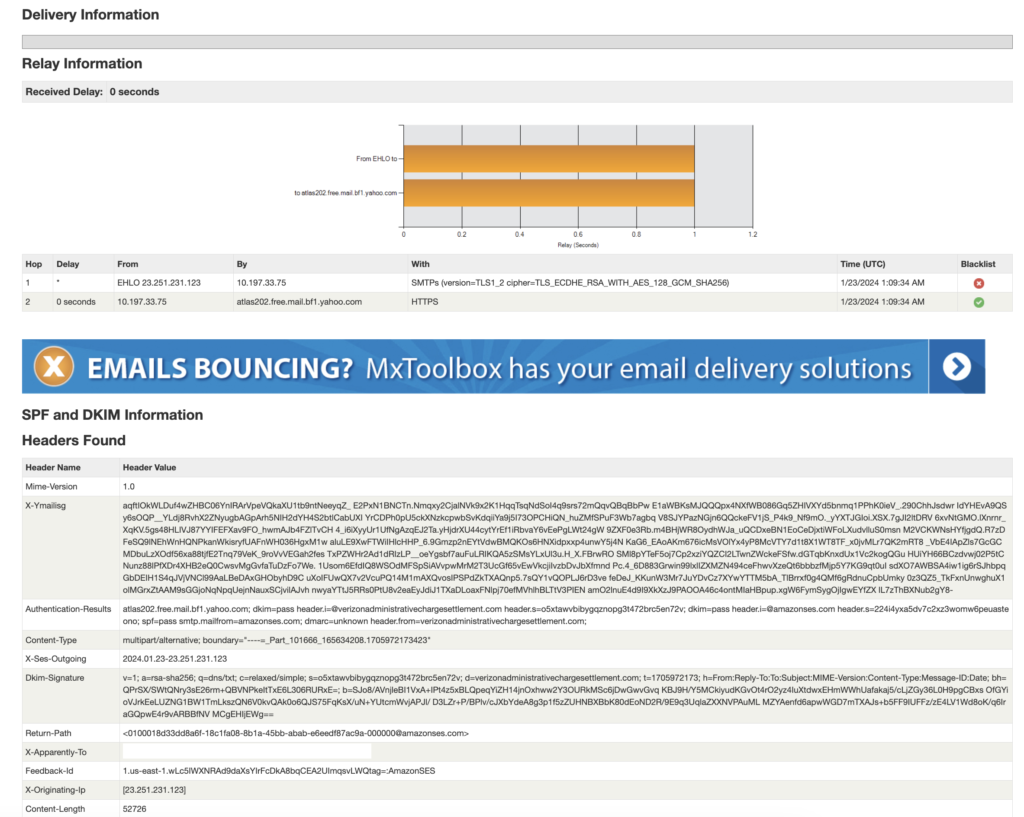
There is a lot of information that might seem to be in different language. In a nut shell, this header analysis shows the originating and destination IP addresses, the senders domain, and what (if any) security protocols are being utilized by the sender.
The two features to look for here are SPF and DKIM. SPF is Sender Policy Framework and DKIM is Domain Keys Identified Mail; these two email authentication types together are commonly known as DMARC, Domain Message Authentication Reporting. DMARC is a commonly used protocol implanted by most trustworthy sources. The use of DMARC is not the holy grail sign that the email is safe, it is simply one more factor to help you identify the possibility of a malicious email. Malicious entities can also implement this. That is why it’s important to take note of a variety of the header values in order to make a better critical analysis. After providing text to the header analysis, it will summarize features that are recognized as compliant with a green check or not compliant with a red x. An organization with a well-versed IT and security team usually employ DMARC. Here we are specifically looking for “dmarc-info” and “dmarc-policy”. Now, the absence of DMARC is not an absolute indicator of a malicious email. It is a tool for your toolbox. Several other features will be summarized such as Message-ID, originating-ip, Mailer, Received-SPF, MS-Has_Attack.
For example, this email has several red flags or indications of a malicious email.
The sender is contact VerizonAdministrativeSettlement.com. Most reputable organizations pay for their own domain, it is more likely that a legitimate Verizon email would use a Verizon URL or domain (even if they did use an Amazon services). The use of a globally known and trustworthy name is an example of how malicious parties prey upon the untrained computer user.
Look at the hops . The red X underneath blacklist indicates that either the domain or IP from this sender has already been reported and is marked blacklisted for some reason. This reason in particular is due in the senders domain and/or IP being associated with spam.
Unfortunately this email did employ DMARC. If you come across a suspect email, run the header analysis, and look for DMARC (SMF and DKIM). If the analysis results lack DMARC, use that alongside the other evidence and make the best decision possible. If it were me, this email should be deleted and perhaps even block the sender.
The financial compensation for this settlement is $100. That is a small reward for the risk of providing your personal information.
Other (Easy to Use!) Tools
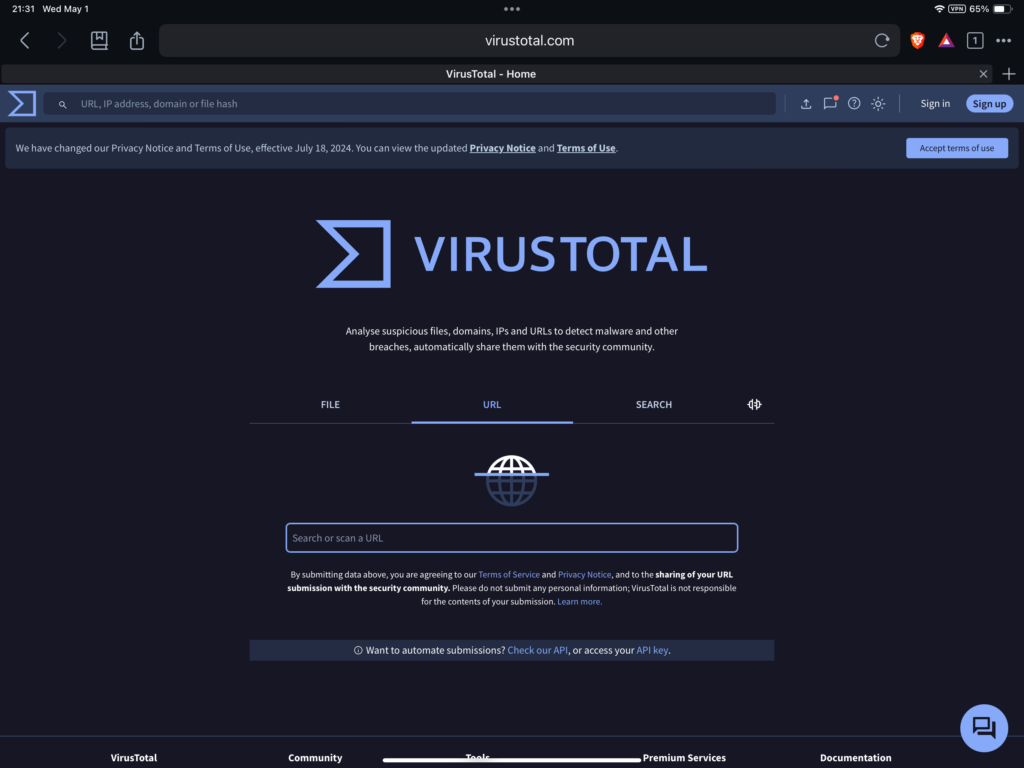
URL Analysis w/ VirusTotal
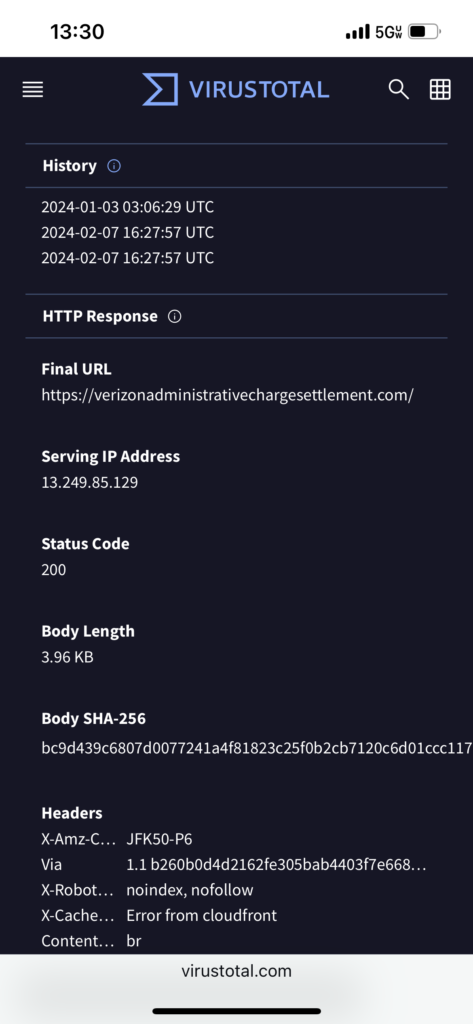
This is a pasted description provided by VirusTotal (VT) from their webpage. It was worded perfectly, I didn’t dare take away any component by attempting to explain it in my own words. Here it is, “Upon submitting a file or URL basic results are shared with the submitter, and also between the examining partners, who use results to improve their own systems. As a result, by submitting files, URLs, domains, etc. to VirusTotal you are contributing to raise the global IT security level.” This is another simple tool for your tool box. There are a few options to consider when coming across a questionable URL or file. The most simple choice is to not use it or delete it but if it isn’t that simple, now you have VT in your figurative toolbox. Copy and paste a URL or upload a file. VT will assist in your decision making process. Although VT has a vetted process in the results they are providing, it is ultimately the end-user (YOU and me) who need to make the best decision. It is a good idea to to go back, review, and implement the beginner tips and tricks. For example, you have received an email from Verizon. It seems legit but their provided URL and a friendly short URL do not match. The blue link simply says Verizon. Never use these friendly short URLs. Smartly, you copy and paste that URL into a notepad to view the entire URL. You’re not sure what this all means but you are sure that it isn’t making sense and is suspect. Copy and paste the entire URL into VT. Let’s test the URL from the same email we used for the header analysis <http://verizonadministrativechargesettlement.com>.
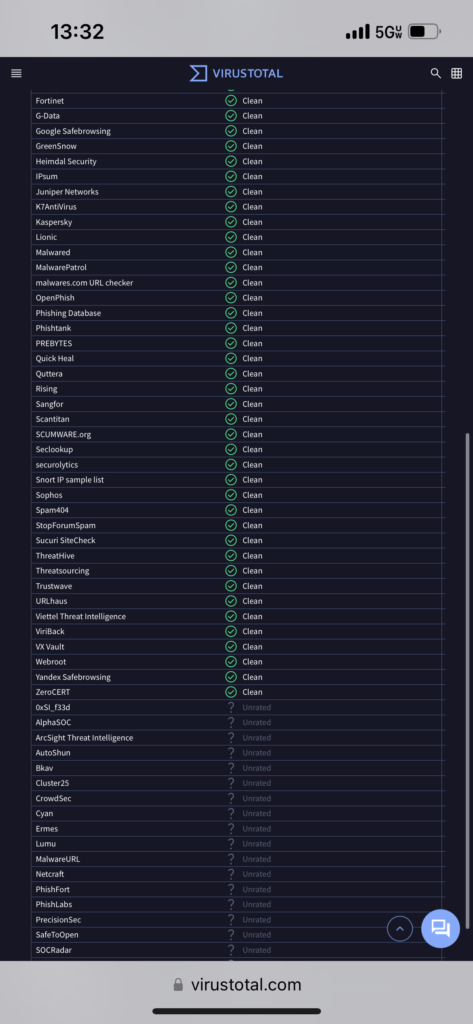
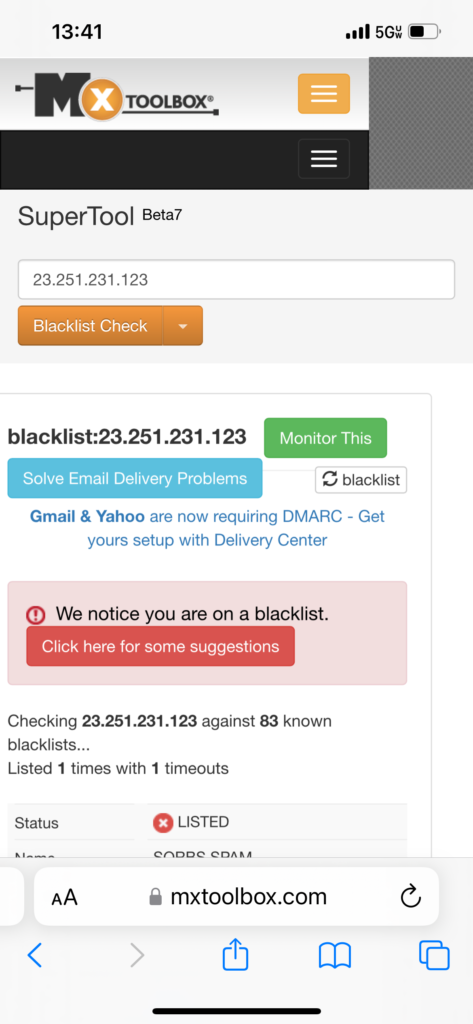
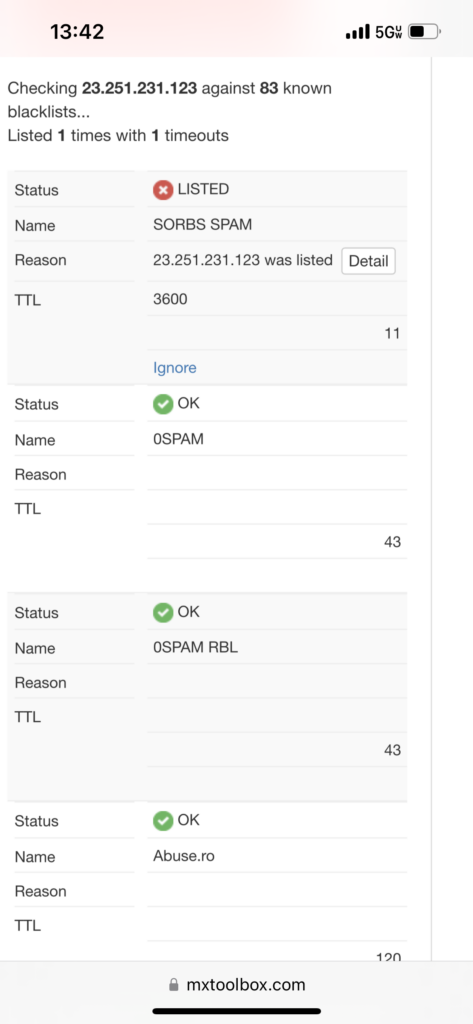
SuperTool w/ VirusTotal
VirusTotal (VT) also has a free beta SuperTool. It will check any URL, domain, or IP for reported suspicious activity. The senders IP from our email has previously been scanned and is associated with spam.
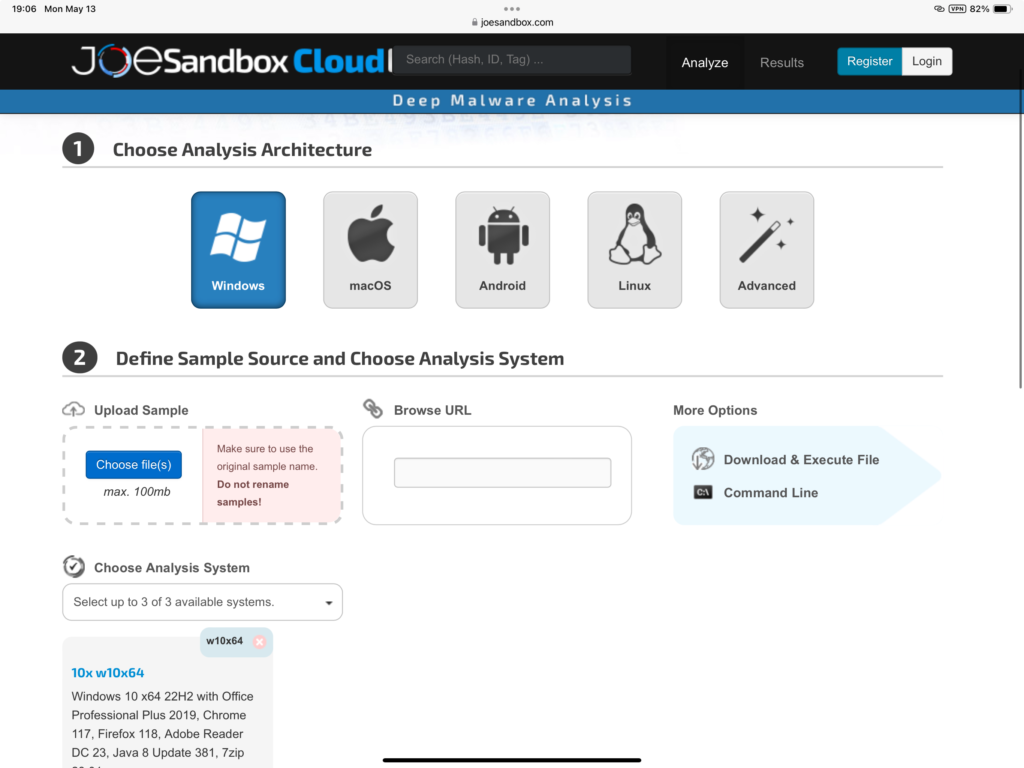
Joe Sandbox
Joe Sandbox also scans URL’s like VT but it additionally can scan suspicious files. Users will need to create an account to use the free version. What is neat about the Joe Sandbox tool is that it will show you the what-if of the executed file.